How do you like to pay?
According to NFC World, 39% of US consumers admit they prefer mobile payments if many apps & stores accommodate it for transactions.
Mobile payment processing has become integral to modern-day transactions, enabling customers to pay anytime, anywhere, with a few clicks. It is the lightest wallet to carry. With the rising popularity and usage, merchants must invest in integrating mobile payments.
However, with convenience comes risk, and merchants must prioritize payment gateway security for mobile devices to protect their customer’s sensitive information and avoid breaches.
This blog post will cover the guiding principles of secure payment processing and best practices for banks to build a solid and secure mobile payment processing infrastructure.

Key Principles and Guidelines for Secure Mobile Payment Processing
In simpler terms, a secure payment processing system, be it for mobile or any other online transaction, deals with:
- Fraud
- Cybercriminals
- Non-compliance
So, what are the key principles to tackle these three factors?
Encryption and Tokenization
A report by Varonis reveals that 7 million unencrypted data records are compromised every day. Encryption must be a top priority. All transaction information must be encrypted to increase the complexity of the code so that hackers and unauthorized parties do not intercept the details.
Two-Factor Authentication
Two-factor authentication adds another layer of security which initiates a transaction only after the user confirms on both checkpoints. It usually includes a combination of password or PIN and biometric factors to ensure the person on the other end is an authorized party.
PCI Compliance
Banks must integrate online payment processing systems that comply with industry standards and regulations, like the Payment Card Industry Data Security Standard (PCI DSS), to ensure that their mobile payment system is secure.
Infrastructure Security and Reliability
The rules and regulations keep changing, so merchants and system providers must stay in touch with industry standards and upgrade their systems with the latest technology and plugins to protect against any vulnerabilities, attacks, or fraud.
Ensure that the network, payment gateway, and technology are updated and meet industry standards.

Best Practices for Merchants to Ensure Secure Mobile Payment Processing
The following are nine best practices for banks and merchants to build a solid and secure mobile payment processing system for their customers:
Implement Strong Password Policies
Develop a password protection policy system to avoid unauthorized access. Ensure that your customers and employees use complex passwords and regularly change them. Ensure no person exchanges or shares their password with others.
Build a Multi-Layered Security Infrastructure
Develop a mobile payments technology infrastructure for your hardware, software, and network with additional layers to ensure the data and transactions are secured even if one layer of security is exposed or weakened. Use firewalls, anti-virus software, multi-layered authentication, plugins, alerts, and detection systems.
Partner with a Secure Payment Gateway
Partner with PCI-compliant third-party providers who employ the best measures and use encryption and tokenization to safeguard customers’ private information. Always look for a NACHA Preferred, PCI DSS Certified third-party payment processing solution provider.
Limit the Day-to-Day Transaction
Consider the nature of your business and average transactions to determine a limit on transactions based on the time period or amount of a transaction as a measure for mobile payments fraud prevention. You can also install systems for notifications, emails, and alerts for any suspicious activities.
Implement Session Timeouts
Session timeouts automatically log a customer out of their account after a certain period of inactivity to keep it locked and safe from unauthorized parties. When a customer/user does not take action on their account, the access to their device is automatically locked, making it difficult for an outsider to tinker with it.
Manage Access Control
A not-so-common mobile payment security measure is access management. Limit access to data like customer personal information depending on employees who require it to perform their daily duties.
Offer Regular Security Training for Employees
Conduct training sessions for employees on payment security best practices, such as identifying phishing scams, protecting payment data, and the latest discoveries and trends to keep them equipped with the system and prevent security breaches resulting from employee errors or negligence.
Educate Customers on Security
Tread the extra mile and educate your customers about the need for implementing new models, measures, and practices. Additionally, advise them to create strong passwords, use secure mobile networks, and avoid public Wi-Fi when making payments. This will strengthen trust and customer satisfaction in your brand’s favor.
Monitor and Update Payment Systems and Data
Mobile technology is revolutionizing the industryr faster than ever. Keep a tab on the ongoing changes and implement the latest security patches and software updates. Deploy fraud detection software to identify unusual transaction patterns and build a system to take immediate action against data breaches or fraudulent transactions.
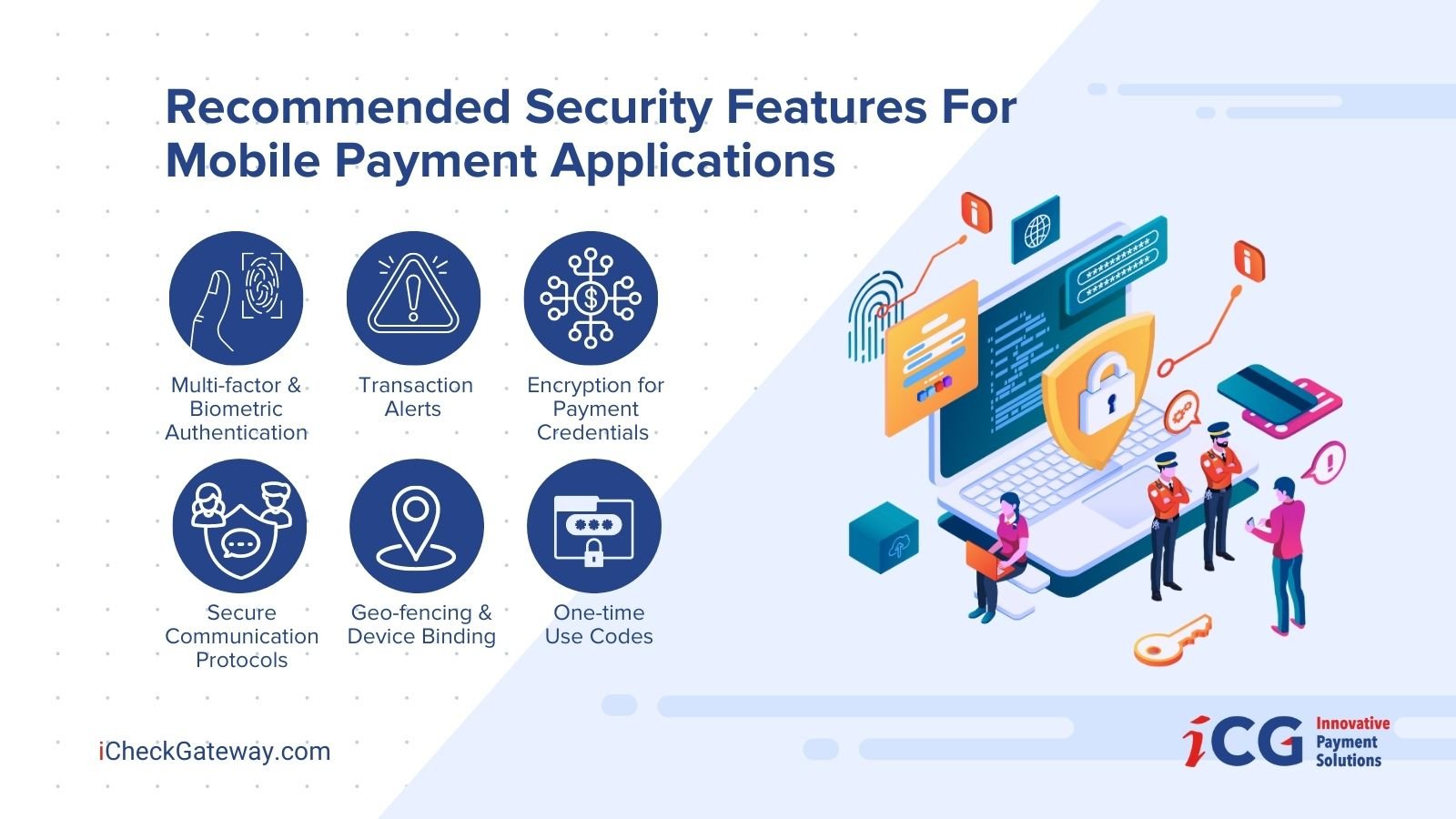
Recommended Security Features for Mobile Payment Applications
70% of fraud is accomplished through mobile applications. This makes your first priority building a mobile application that your customers can use confidently. At iCheckGateway.com, we recommend that our clients include these features in their mobile payment applications:
Multi-Factor and Biometric Authentication
Having two-factor authentication means adding another layer of protection. Most preferable is to have a combination of a password and biometric verification as it is harder for hackers to steal such information.
Biometrics rely on unique physical characteristics, like fingerprints or facial recognition, to verify the user’s identity, making it more secure than traditional passwords.
Transaction Alerts
Send alerts to your customers when they pay with their mobile payment application via email or text. Instant notifications can help users identify and report any unauthorized transactions fast.
Encryption for Payment Credentials
Payment credentials, such as credit card numbers, should be stored securely in the mobile device using encryption or tokenization to ensure they are protected from hackers.
Secure Communication Protocols
Mobile payment applications should use secure communication protocols, like SSL/TLS, to ensure payment data is transmitted securely.
Geofencing and Device Binding
Limit the location and device of transactions using geofencing and device binding. GPS technology ensures transactions are only processed in specific locations, preventing unauthorized access and reducing the risk of fraud.
One-Time Use Codes
Generate one-time use codes for real-time account verification and transactions and send them to the user’s trusted device. Since the code can only be used once and expires after a set period of time, merchants can significantly reduce the risk of fraudulent activities.
What Are Successful Examples of Mobile Payment Security Strategies?
Apple Pay, Samsung Pay, PayPal, and Venmo have developed powerful and secure payment processing strategies to offer seamless mobile payment experience to their customers.
Apple Pay is the most popular and widely accepted digital wallet in the U.S., whose popularity primarily comes from consumers building their Apple ecosystem with other Apple devices. Customers and merchants can integrate it with their other Apple devices, like the Apple Watch, making contactless payments more efficient than any other provider. Apple has also built a secure processing system with tokenization, biometric authentication, geolocation tracking, and device-specific security measures.
Another popular mobile payment processor is PayPal, which works on most devices in the United Stats and is therefore a consumer favorite.
Secure Your Mobile Payment Processing
Secure payment processing on mobile devices is critical for protecting sensitive data, complying with regulations, preventing financial losses, and improving customer experience, especially when we expect an exponential increase in mobile payment transactions.
According to Statista, the total transaction value is expected to reach US$ 3,528.00bn by 2027. Banks and merchants must prioritize payment security on mobile devices to build trust, reputation, and loyalty while staying ahead of evolving security threats.
If you have any questions or doubts, reach out to our experts at iCheckGateway.com. We will be happy to help you out.



